With the introduction of network-based ransomware viruses, attackers may now begin campaigns without the need for human participation, according to the Cisco Annual Cybersecurity Report.
There are a lot of hackers who are behind your data to steal it. All you need to do is to understand the different types and make sure you do not invite unnecessary problems. Thi can lead to a breach in your system.
Malicious actors frequently seek ransom or other forms of financial gain, however assaults can be carried out for a variety of reasons, including political action.
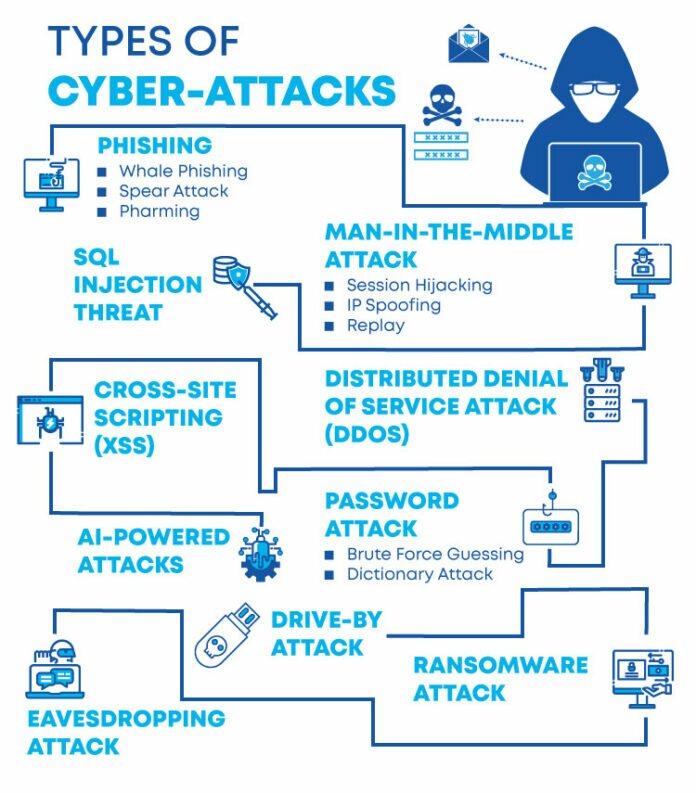
The Top 10 Most Common Cybersecurity Attacks
Let us have a look at the different types of cyber attacks:
Viruses and malware
Malware refers to a wide range of threats, including spyware, viruses, and worms. When a user opens a “planted” harmful link or email attachment, which is used to install malicious software within the system, malware exploits a vulnerability to infiltrate a network. Malware and malicious files on a computer can do the following:
- Access to the network’s vital components is denied. Information is obtained by accessing data from the hard disc.
- The system will be disrupted, if not rendered unworkable.
DOS (Distributed Denial-of-Service) Attack
DoS attacks overwhelm resources and bandwidth by flooding systems, servers, and/or networks with traffic. As a result, the system is no longer able to process and fulfil genuine requests. There are distributed denial-of-service (DDoS) attacks in addition to denial-of-service (DoS) assaults.
DoS attacks overwhelm a system’s resources in order to slow response time to service requests.
Injections into SQL
This form of attack generally entails inserting malicious code into an open comment or search box on a website. SQL injections may be avoided by utilising secure coding methods such as using prepared statements with parameterized queries. This type of attack will cause a huge issue in the coding of your drives and will lead to data leak.
Zero-day vulnerability
Exploiting a network vulnerability while it is new and recently publicised — before a patch is available and/or applied — is referred to as a Zero-day Exploit. Now these attackers can prove to be really dangerous if you keep your files at one place. As a result, combating zero-day threats necessitates continuous monitoring, proactive detection, and flexible threat management techniques.
Attack on Passwords
You must keep in mind that your password must not be shared on any device. An attacker can obtain access to private or vital data and systems, as well as influence and control them, by gaining access to a person’s password. You must keep your passwords very difficult and only to the limit that you understand and remember them. Do not make it so simple that anyone else can guess it.
Conclusion
These are some of the different types of cyber attacks. All you need to do is to follow these and keep it in mind to stay away from them. You can also get in touch with the team of Appealing for better clarity.









![Anso FG Reviews: UPDATED 2024 [ansofg.com] Anso FG Reviews UPDATED 2024 [ansofg.com]](/wp-content/uploads/2023/12/Anso-FG-Reviews-UPDATED-2024-ansofg.com_-100x70.png)







